Hacker Persona: From Gamer to Cybercriminal, A Natural Evolution Spurred by COVID Lockdowns
Concealing myself behind multiple identities, I have been hunting cyber threats on underground platforms for several years, monitoring and interacting with hackers and attackers focusing on online applications. I started monitoring these threat actors since I was a Junior CTI (Cyber Threat Intelligence) researcher and since the tracked subjects were still Script Kiddies (skids). During my research, three questions persistently preoccupied my thoughts:
- Where do they come from?
- What are they aiming for today?
- What personality traits and psychological motivations got them here?
In this ‘Hacker Persona’ series, I will take you back to a ‘high school reunion,’ focusing on the gamer persona and answering the question ‘how (some) gamers evolve from nice fellows into cyber criminals?’
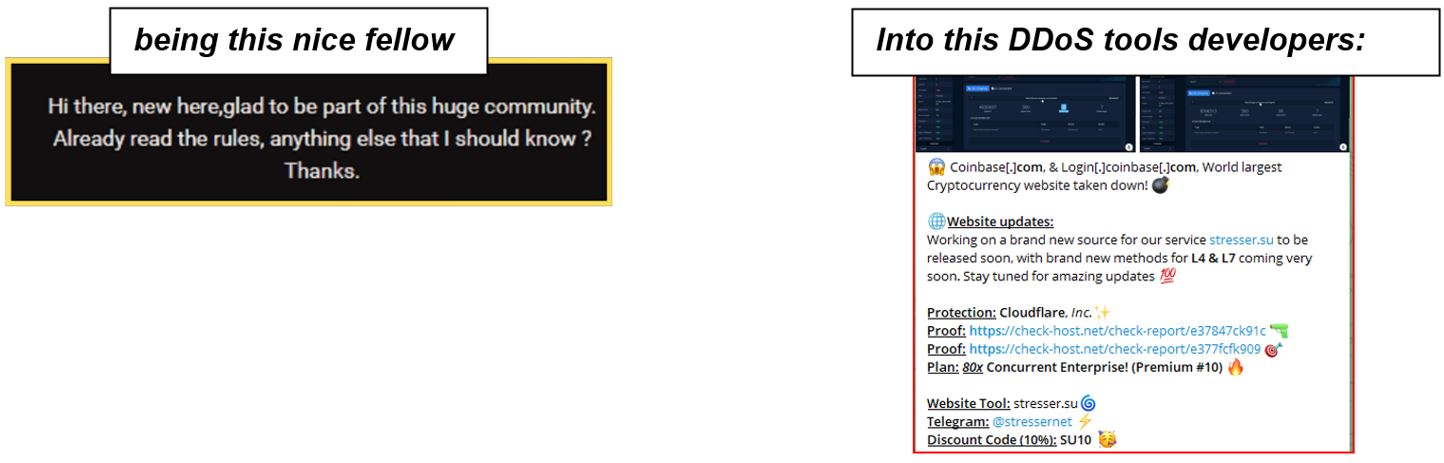
Figure 1: How a gamer turned from nice fellow to cyber criminal
This is the first blog in the series, covering the evolution of ambitious gamers turning into threatening application attackers. The findings are based on an observational study across four underground platforms and a sample of 26 attackers who began their ways as gamers and currently maintain reputable application hacking services on the underground.
By the end of this blog, you will have a better understanding of:
- How gaming can ‘accidentally’ funnel people into hacker marketplaces
- How COVID lockdowns incubated one of the most significant hacker baby booms to date
- The entry gate to the dark side: how are gamers are exposed and start to engage in application hacking
The Gaming Industry: from buy-me-if-you-can into Free-to-Play, Paid-to-Stay
It is impossible to understand the next-gen hackers’ mindset without understanding their world. Here is a crash course on gaming and how the gaming industry fell in love with the freemium business model and how this love affair created new opportunities for application hackers. Let us recap the fundamental changes in the gaming world.
If you spent your teenage years playing PC games in the 90s like me, you remember buying games or downloading a crack or license generator through Kaza, Emule, BitTorrent, LimeWire or Gnutella (choose your age). Your journey into accessing new games did not involve engaging underground hackers. Today, however, if your kid is trying to get a cheaper version of their favorite game, they will most likely buy them from an underground marketplace, the same place where breached credentials and personal information are offered for free.
Why does the road to a cracked gaming account change from “playing in the park” to “walking in the wrong neighborhoods?” The gaming industry changed its business model and monetizing schemes for games. Let us break it down.
Architecture: games used to run entirely locally, requiring expensive hardware with price tags that kept many potential PC gamers away. Currently, the gaming industry uses the cloud, hosting high-end GPUs that render and encode graphics and stream the visuals, while high-end cloud CPUs run the simulation and game logic. Such cloud workloads allow gamers high-quality access to gaming experiences without having to invest in expensive hardware. Another key strategic advantage of the cloud architecture is that the game can get updates such as additional content; therefore, the game never ends.
Business model: Slowly but steadily, the gaming industry fell in love with the freemium business model. Instead of pre-paid experiences, users can play for free and purchase in-game virtual goods with micro-transactions. Some games leverage a pay-to-win model where users can play for free, but to achieve a higher rank, get one of the ‘cool’ skins or a better sword that deals more damage, users need to pay. Payments can be made through micro-transactions, leveraging ‘real’ money to buy in-game currency, or by earning in-game currency through grinding.
In-game Economy: To support this new business model, game publishers created an “in-gaming economy” that incentivizes players to stay engaged in their games. In this model, gamers are paid virtual currency specific to the game for every action performed in the game or every level crossed. This in-game currency allows the purchase of gaming assets such as ranks, skins and weapons. While assets may not hold value in the real world, they are highly desired by young gamers trying to gain status and respect from their friends and the gamer community. Like expensive watches and luxury vehicles are status symbols for wealth in the real world, gaming assets provide social status to gamers.
The combination: Games that implement a successful in-game economy, multiplayer platforms hosted in the cloud, and an active gamer community like Roblox, Star Citizen, Counter Strike, Fortnite, Call of Duty Warzone, PUBG Mobile, etc. can quickly gain billions of gamers combined. Minecraft, the famous 16-year-old game, gathered over 300 million users in total and Roblox reaches over 70 million daily active users worldwide. When the gaming industry saw these numbers, they quickly adopted them.
The Lockdown Baby Boom
Thanks to the core changes in the gaming industry, it was the only industry that was well-prepared for a pandemic. By the time the global pandemic sent teenagers all over the world into lengthy quarantines with half-functioning educational frameworks, the gaming industry provided virtual hang-out spaces and became the social equivalents of the shopping malls in the 80s.
PC games turned into endless shopping malls where you do not have to pay at the entrance because they spend while they are in and are encouraged to stay. Modern online games allow people to co-operate or compete with other people, without physical or geographic boundaries. Gamers do not have a ‘pause’ option without getting killed in the game or being summoned by their friends and community. Therefore, there is no ending. If you are a parent to a gamer, you probably understand this very well.
Low barrier of access: the access to gaming moved the threshold from owning 1000-2000$ hardware and 60$ for a game to 0$ for the hardware thanks to Cloud computing and 0$ for the game, a descend mobile phone is all that is required to get access to one of the many gaming titles with large communities.
The onset of COVID-19 coincided with a significant growth in video game usage, with 2.7 billion players in 2020. Gaming and streaming platforms provided a social and safe alternative during lockdowns and social isolations.
From Game Cracks to Account Takeover
What about those gamers that seek to get fast and free status and replace their “noob” avatar with a highly ranked one?
Ten years ago, the goal was to gain access to games illegally while modern gamers’ goal is to access highly ranked accounts with high currency balances. As a result, hackers have shifted their focus from game cracks and key generators to breaching gamer accounts. This created a high demand for stolen gamer accounts on underground marketplaces and criminals rushed to supply this demand.
The figure below shows that almost a third of the “cracked.io,” a notorious marketplace, referrals come from gaming-related websites. Furthermore, “lolz.guru,” a gateway marketplace for breached accounts, sees 89% of their referrals coming from gaming-related websites.
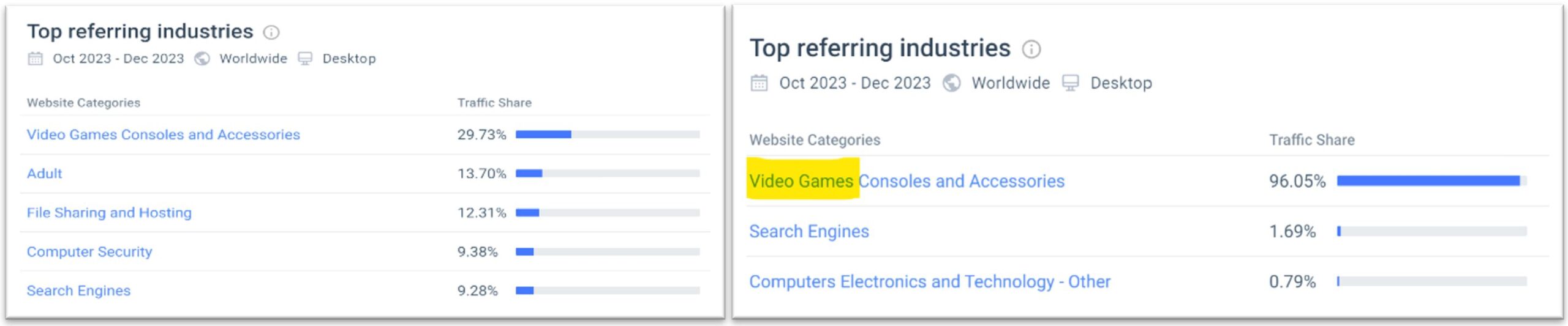
Figure 2: Top referring industries for cacked.io
Figure 3: Top referring industries for lolz.guru
The Gamer-to-Hacker evolution scale
Although less than half of a percent of all gamers start the evolution and an even smaller fraction completes eventually become full-time hackers, it is worth mentioning there are 1.5 billion gamers today and based the latest research papers research papers, it is estimated millions of them have joined since the pandemic. Half a percent represents millions of “new bloods” in hacker marketplaces and several thousands of new tools created.
Who is the “new blood,” and what differentiates them from past generations of application threat actors?
The Gamer Persona
What type of wheat is getting into the hacking marketplace oven?
Mentality: Some of the young future-threat actors spend four to five hours a day for several years on solving problems and overcoming challenges in modern PC games. The daily practice of solving complex problems creates mental resilience, self-learning skills, and a sense of competence, the three cornerstones of developing technical skills in cyberspace.
Motivation: The younger gamer age group is armed with a hunger for success and respect on social media, disarmed from any risk assessment. In my observation, hackers that make the end of the evolution and become full-time hackers began their journey through curiosity and willingness to prove, two massive drivers in the hacking sphere.
Communication: Connected more than ever before, gamers form communities on Discord, follow influences on Twitter and Telegram, learn how to master gaming by watching Twitch all day, brag about their ‘wins’ or ‘cool skins’ on TikTok and cry over their losses on Reddit. Historically speaking, gamers have never been connected like they are now. Telegram and Discord allow anyone to enter communities and some communities are leveraged by gamers to turn to the dark side and get attention and mentoring.
Age: Modern gamers are younger than ever. In the last decade, the average age kids started gaming has decreased to 6 years.
Gamer To Hacker Timeline
Step 1: Exposure – The Gamer’s first exposure to an underground marketplace.
Incentives: low-cost gaming accounts with a high amount of assets (virtual coins/rank/level)
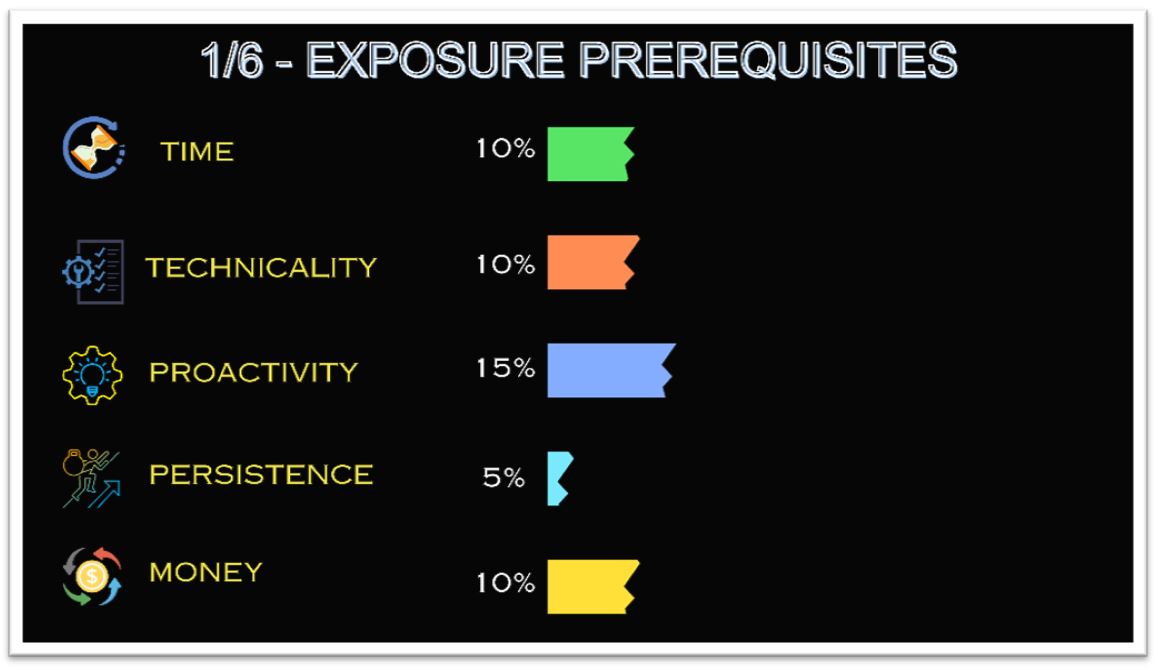
Figure 4: pre-requisites for exposure to underground marketplaces
Underground marketplaces lure gamers with offers of 1$ for breached gaming accounts. One of the gateway marketplaces is lolz.guru, a Russian-speaking marketplace selling breached Fortnite accounts. Right next to the breached gaming accounts, subscriptions are sold to operate Infostealer malware that runs stealthily for months before being detected. Marketplaces like these identified a constant influx of inexperienced users and, over the years, started adopting some of the traits of the gaming world. Each forum member now has a rank, points, levels, and credits. Members are incentivized for their activity, especially for sharing content.
Higher levels and more points will gain members access to more exclusive content.
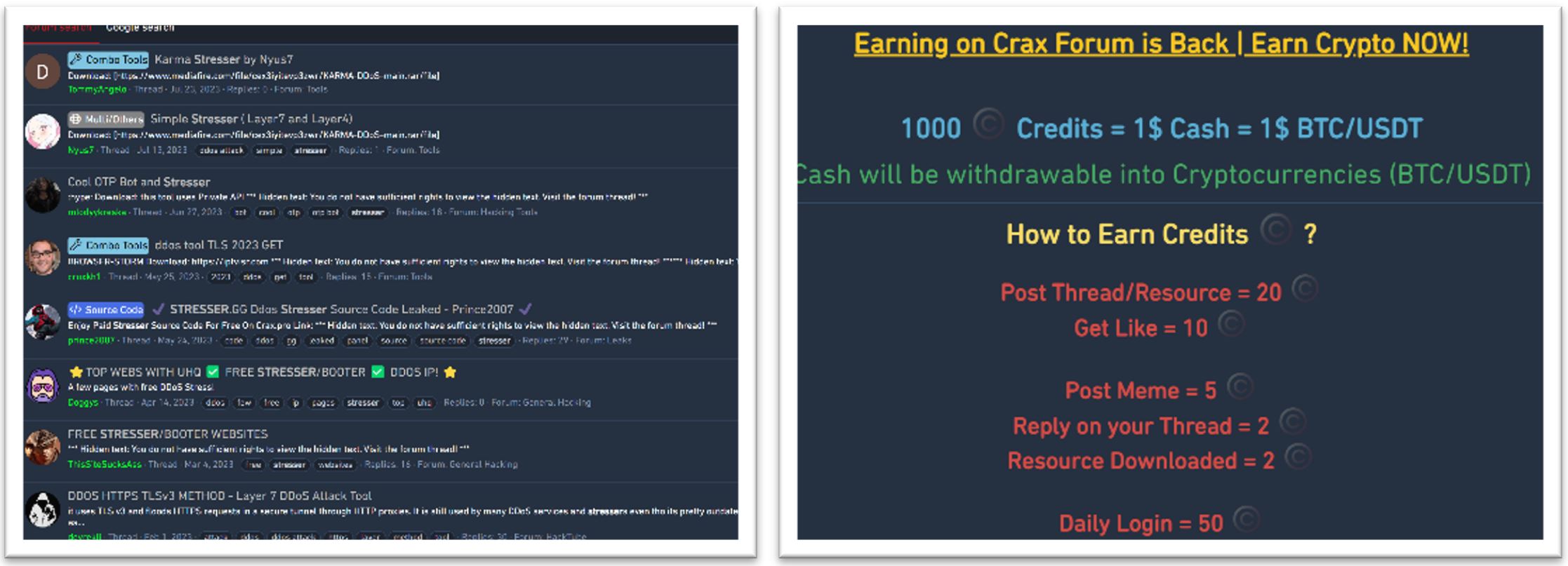
Figure 5: DDoS tools and tutorials shared for free by tool developers and marketplace sellers
Figure 6: crax.pro marketplace credit policy
As can be seen in Figure 5, threat actors that sell hacking tools create hacking tutorials and share assets such as easy target lists for DDoS (Distributed Denial of Service) to gain marketplace credits and attract buyers for their DDoS tools or services. Some threat actors target new and inexperienced members by selling tools that can be found for free in GitHub (i bought a DDoS attack on the DARK WEB (don’t do this) (youtube.com)).
What to expect in part 2
We have covered the foundations of the evolution from gamers to application hackers and the drivers that initiated this evolution. In the second part of the blog series, I will dive into the five steps of the application hacker’s evolution: from choosing their hacking domains and specialties, through developing their reputation up to creating and managing application attack tools as a service.
Stay ahead, stay tuned.
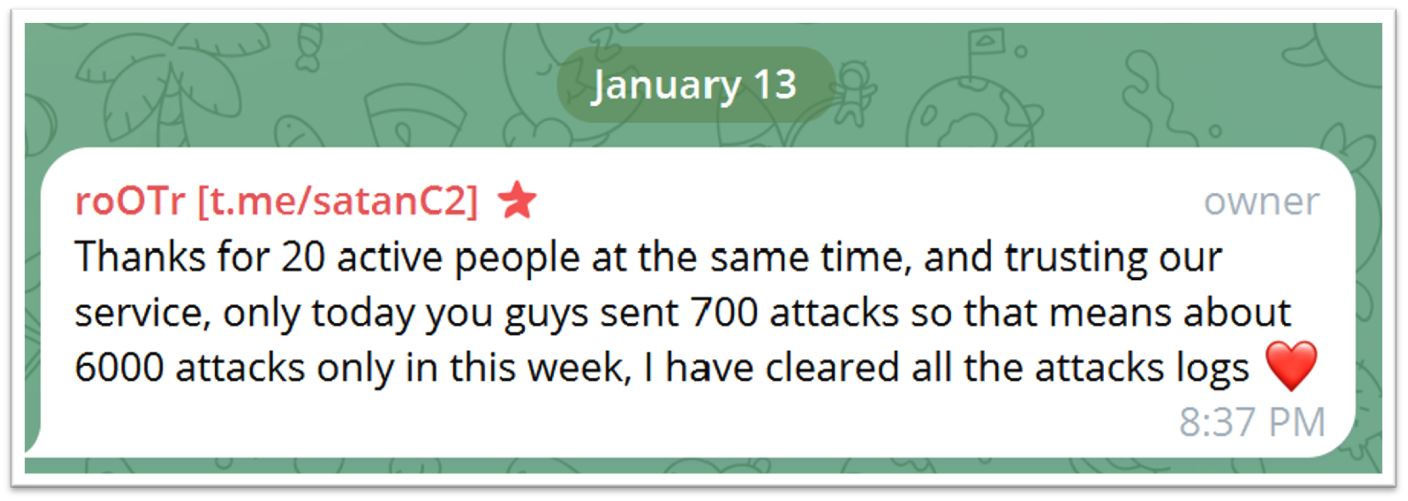
Figure 7: Fortnite gamer turned threat actor bragging about his botnet-as-a-service
Gaming and Covid Stats Resources:
Research Papers:
Increased Gaming in Norwegian Youth: Haug et al. (2022) reported that among boys in Norway, 41% gamed a lot more and 35% a little more during the first lockdown compared to before. For girls, the numbers were 14% and 23%, respectively. These figures could imply a mix of increased gaming among existing gamers and new gamers starting during the lockdown (Haug et al., 2022).
College Students’ Gaming Behavior: Balhara et al. (2020) noted that about 50.8% of participants reported an increase in gaming behavior during the lockdown.
(Balhara et al., 2020).
Gaming Among Children and Adolescents: The study by Donati et al. (2021) focused on children and adolescents’ gaming habits during lockdown in Italy. It does not provide specific percentages of new gamers but indicates a significant increase in gaming activity among this group. The increase suggests that a portion of this demographic might be new gamers (Donati et al., 2021).
Media Reports:
Nielsen Report on Gaming During COVID-19: According to Nielsen, there was a significant increase in video gaming during the COVID-19 pandemic lockdowns. They found that 82% of global consumers played video games and watched video game content during the peak of the pandemic. In the U.S., 46% of gamers reported playing more due to the pandemic, followed by 41% in France, 28% in the U.K., and 23% in Germany. Twitch, a popular gaming platform, saw its viewership in the U.S. more than double during this time period.
UNICEF Report on Screen-Time and Gaming: Digital game distributors such as Steam reported a considerable increase in daily users during the pandemic, from 19 million in early March to a record high of 23.5 million in early April.
Gaming and Health During the Pandemic: A study conducted by New York Tech in partnership with McGill University and Adamas Esports surveyed 897 self-proclaimed gamers worldwide. The study found that casual and competitive gamers reported significant increases in-game time during the pandemic’s initial months. 74.6% of all respondents reported an increase in their gaming time during the pandemic.



