The Democratization of DDoS Attacks: Insights from the IT Army of Ukraine’s Cyber Campaign
In the evolving cyber warfare landscape, the IT Army of Ukraine stands out as a pioneering force, leveraging the collective power of civilian hacker volunteers in the wake of the Russian invasion in February 2022. This grassroots movement has significantly contributed to the democratization of Distributed Denial of Service (DDoS) attacks, a development that carries profound implications for the future of cyber operations, security practices, and digital activism. The IT Army of Ukraine has reshaped the paradigm of cyber engagement, facilitating broader public participation in what was once the domain of specialized hackers.
The inception of the IT Army marked a notable shift towards public participation in cyber activities. Utilizing social media platforms such as Twitter and Telegram, the group disseminated lists of targets, effectively inviting anyone with internet access and a willingness to contribute to join their cyber operations. This open recruitment strategy significantly lowered the barrier to entry for participating in DDoS attacks, allowing individuals with minimal technical expertise to contribute to a collective cyber effort.
Central to the democratization of these cyber-attacks is the IT Army’s active development of existing attack tools to make them more accessible and user-friendly. Volunteers can access a trove of information and installation tools, categorized from beginner to expert, through the IT Army of Ukraine’s website (https://itarmy.com.ua).
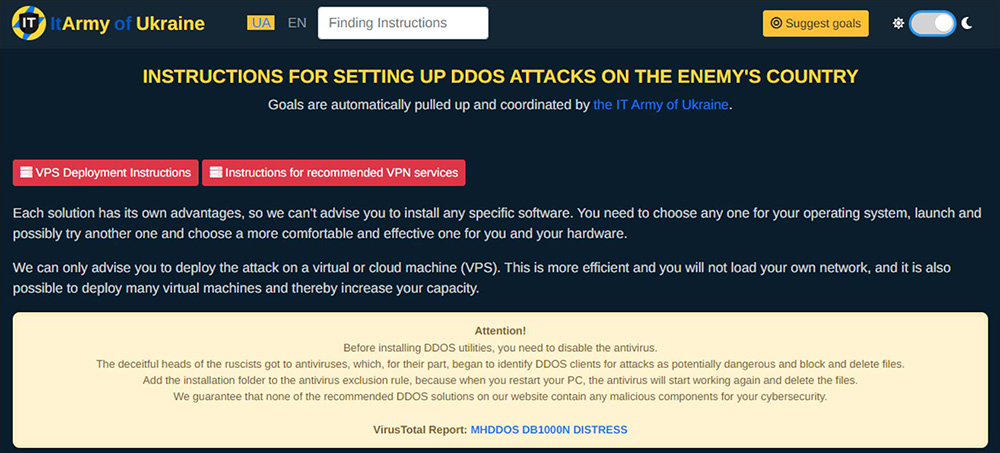
Figure 1: Main landing page for DDoS attack resources provided by the IT Army of Ukraine
The IT Army exemplified the power of crowdsourcing in cyber warfare. The group demonstrated how collective action could significantly impact the cyber domain by mobilizing many volunteers. This model of crowdsourced cyber efforts represents a new form of digital activism, where the strength of a campaign lies in the participation of the many rather than the expertise of the few.
The educational efforts of the IT Army and similar groups have further facilitated the democratization of DDoS attacks. Through the production and dissemination of educational content, these groups have trained volunteers in the technical aspects of cyber operations and in practicing digital activism safely and ethically. This educational dimension has played a crucial role in empowering more individuals to engage in cyber activities with an informed understanding of the risks and responsibilities involved.
Importantly, the activities of the IT Army have led to a broader normalization of volunteer-based cyber operations. This trend suggests a future where participation in cyber campaigns, as a form of support for various causes, becomes a common and accepted form of activism. Such a shift necessitates reevaluating cybersecurity practices, as organizations and governments must now consider the potential for large-scale, volunteer-driven cyber operations that can be mobilized quickly and with significant disruptive potential.
The IT Army Kit
The IT Army of Ukraine’s “IT Army Kit” represents a strategic initiative to lower further the entry barrier for volunteers willing to participate in cyber operations against targets associated with adversarial entities. This kit is essentially a collection of tools, resources, and guidance designed to enable individuals, regardless of their technical expertise, to contribute to cyber efforts effectively.
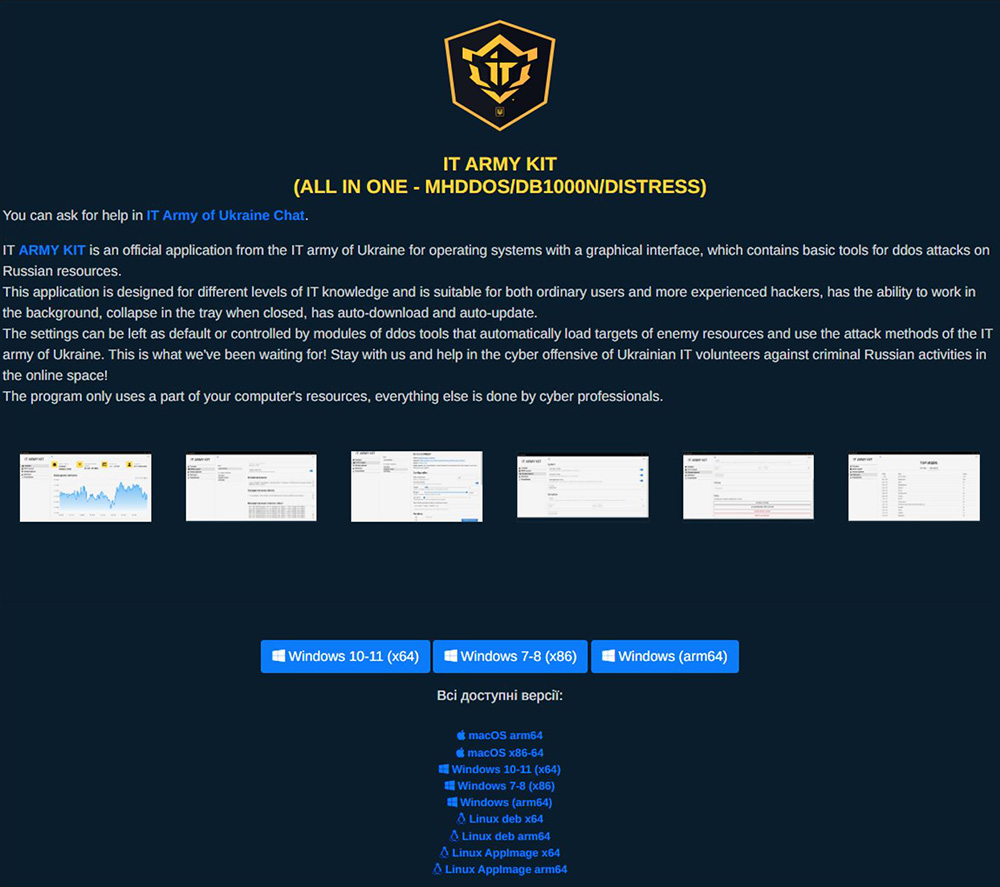
Figure 2: IT Army Kit, the all-in-one IT Army of Ukraine DDoS attack tool
The kit provides access to software to conduct effective DDoS attacks, including improved versions of the open-source attack tools MHDDOS, DB1000N (also known as “death by a thousand needles”) and Distress.
After following the installation instructions provided on the website, a graphical user interface allows the volunteer to select and configure a particular attack module and start attacking targets. The IT Army Kit automatically downloads and maintains a list of targets curated by the IT Army of Ukraine administrators.
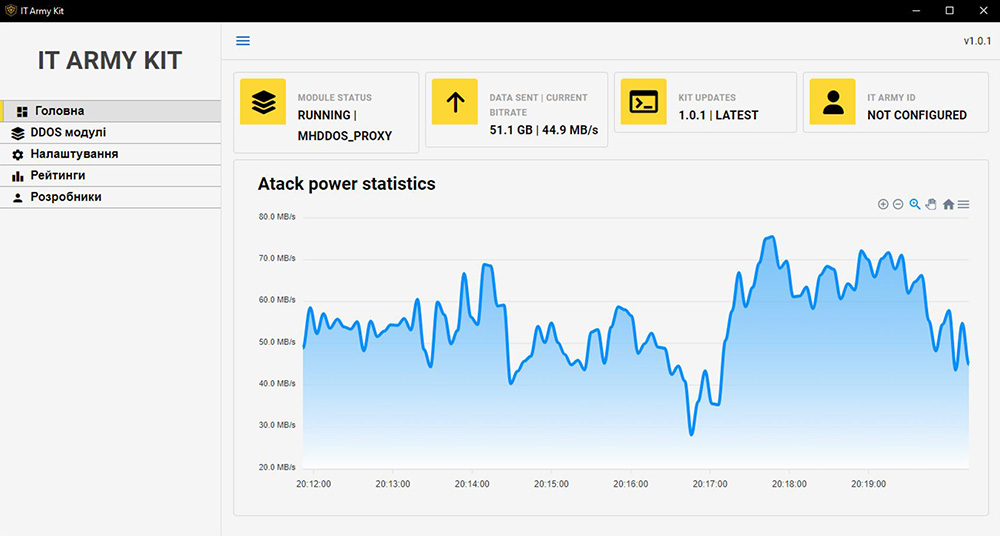
Figure 3: IT Army Kit GUI – main screen
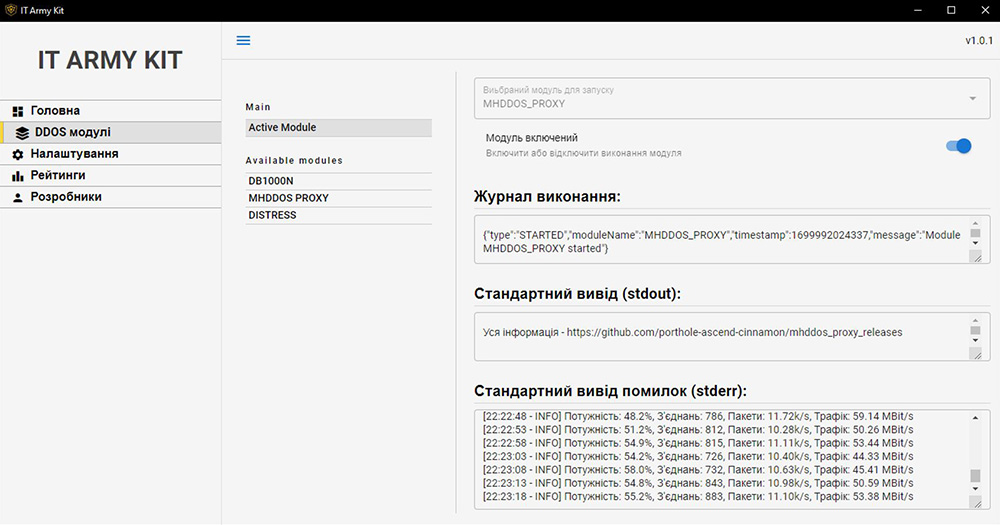
Figure 4: IT Army Kit GUI – DDoS module selection screen
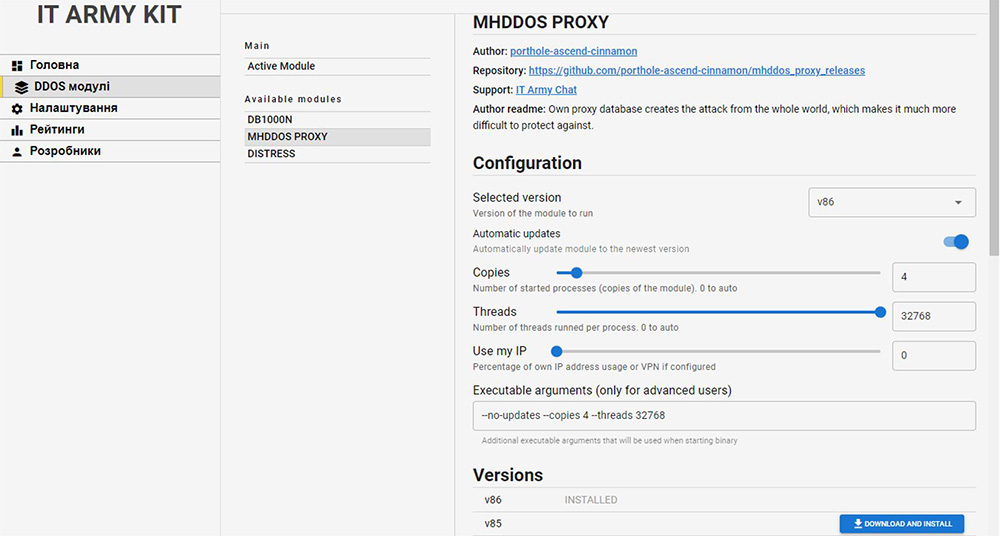
Figure 5: IT Army Kit GUI – DDoS module configuration screen
Volunteers can schedule attacks, to prevent them from interfering with work or disrupting Netflix family movie night. The tool also includes the ability to perform automatic updates as new versions get published by the IT Army.
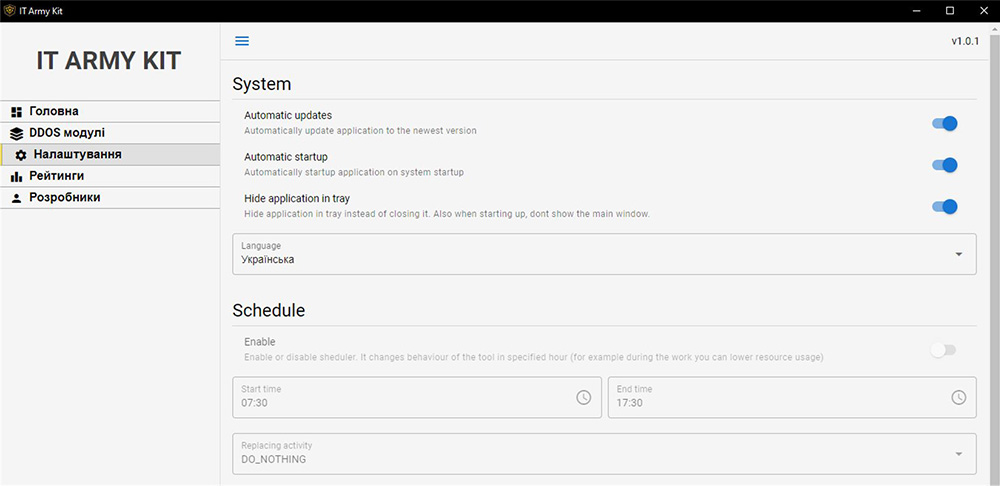
Figure 6: IT Army Kit GUI – system settings for scheduling attacks, launch at start and automated updates
ADSS & Expert Tools
The IT Army provides an Automatic DDoS Server Starter (ADSS) tool, a deployment script that downloads required packages and automatically configures a Linux-based system to transform it into a dedicated DDoS attack node based on MHDDOS. The IT ARMY also provides links and commands to docker images of each individual attack module for more experienced volunteers. These tools include the official IT Army MHDDOS_Proxy attack tool written in Python, the DDoS tool Death by a 1000 needles written in Go and maintained by Arriven, and Distress, a tool written in C that performs TCP and HTTP flood attacks and can leverage Tor egress nodes to conceal its attacks.
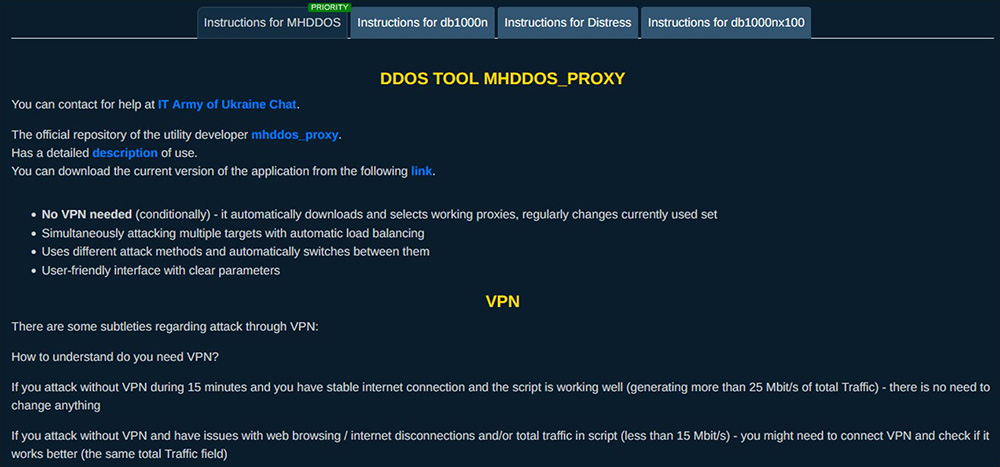
Figure 7: IT Army of Ukraine Expert Tools
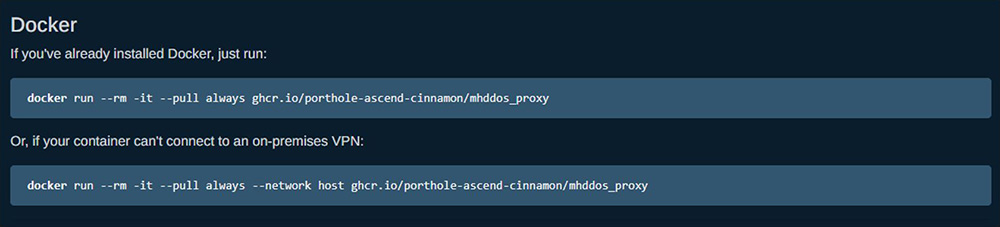
Figure 8: Commands to launch a docker instance running the official IT Army of Ukraine MHDDOS_Proxy attack tool
Leaderboards to Foster Competition
The IT Army of Ukraine leverages leaderboards to incentivize participation and build engagement amongst its volunteer community. The website of the IT Army contains a leaderboard section that is updated several times per hour with weekly statistics of the most active volunteers.
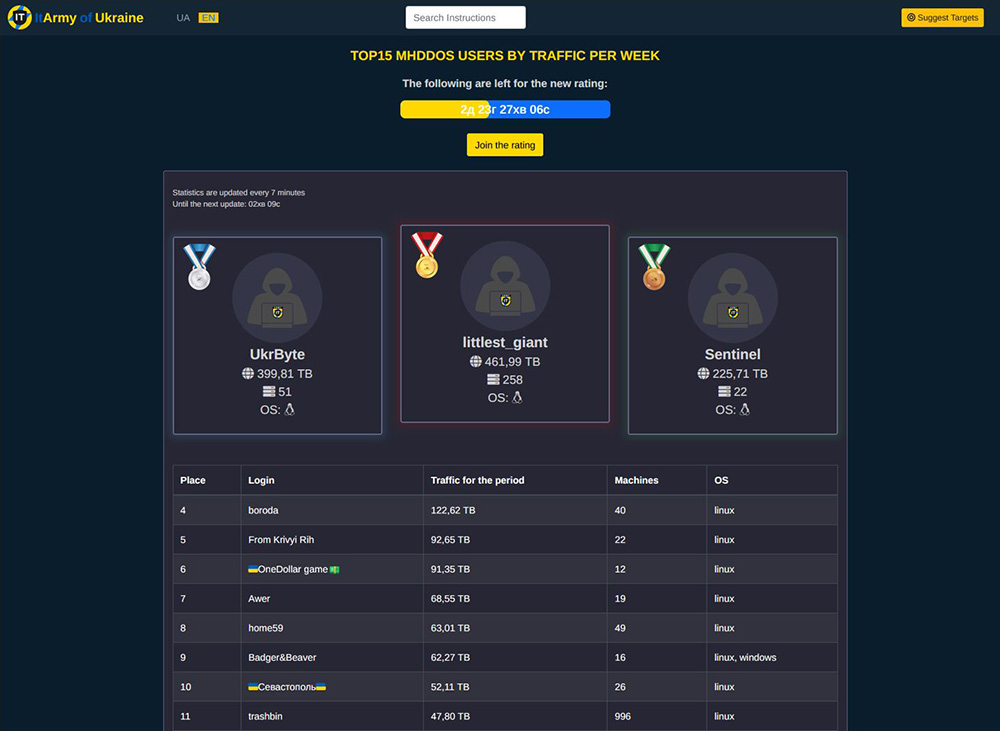
Figure 9: IT Army of Ukraine MHDDOS Leaderboard
The screenshot in Figure 9 was taken at a moment when there were about 3 days left in the weekly statistics period. The leader, ‘littlest_giant,’ generated a total of more than 460 terabytes (TB), representing an average of 115TB per day using a Linux infrastructure consisting of 258 servers. ‘UkrByte’ placed second for the week and generated a total of almost 400TB or an average attack volume of 100TB per day, contributing 51 Linux servers to the objectives of the IT Army.
To reach status and get mentioned on the leaderboard, volunteers can receive an anonymous identifier (IT Army ID) by registering through the Telegram channel ‘@itarmy_stat_bot.’
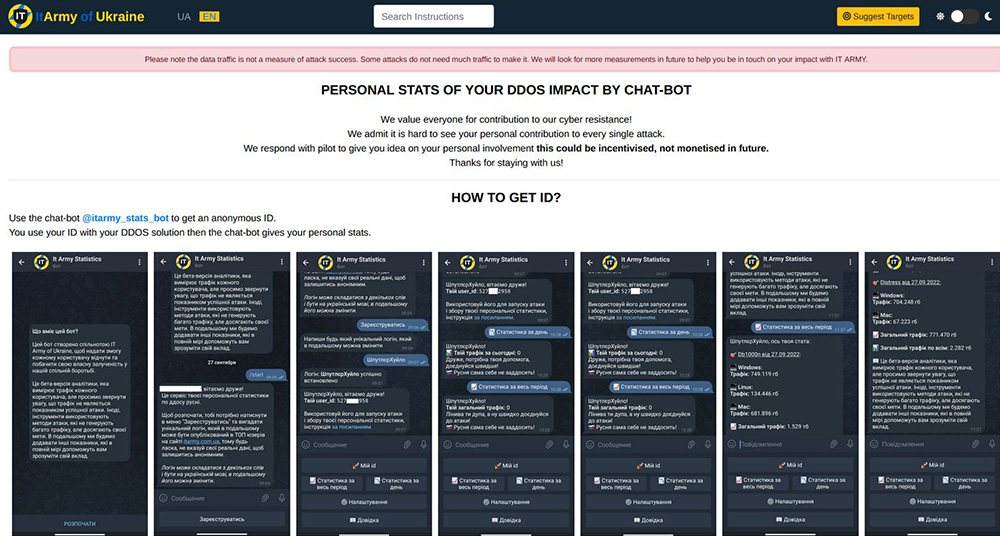
Figure 10: Instructions how to apply for an IT Army ID to get a mention on the leaderboard
The IT Army ID can be configured in the IT Army Kit on the settings page or supplied as an argument to the IT Army maintained command line tools.
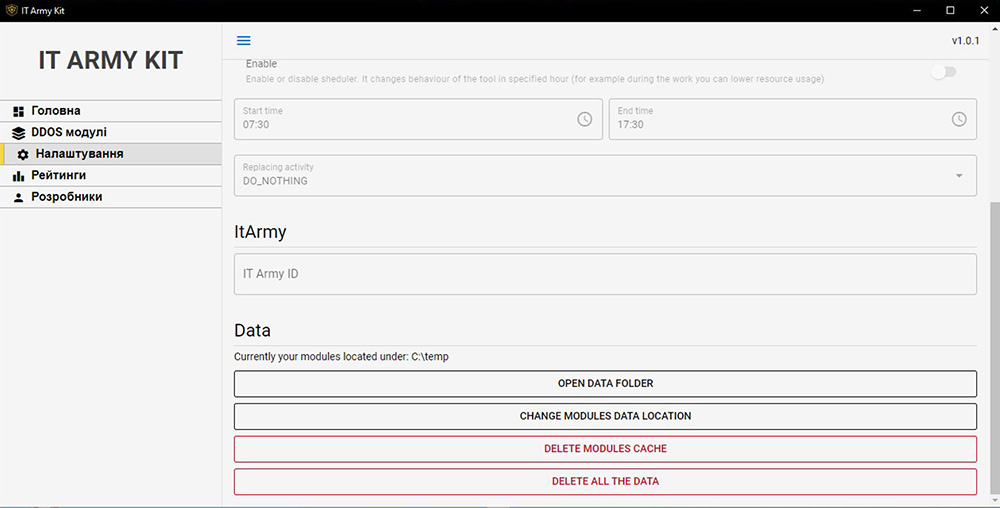
Figure 11: IT Army Kit configuration of the IT Army ID
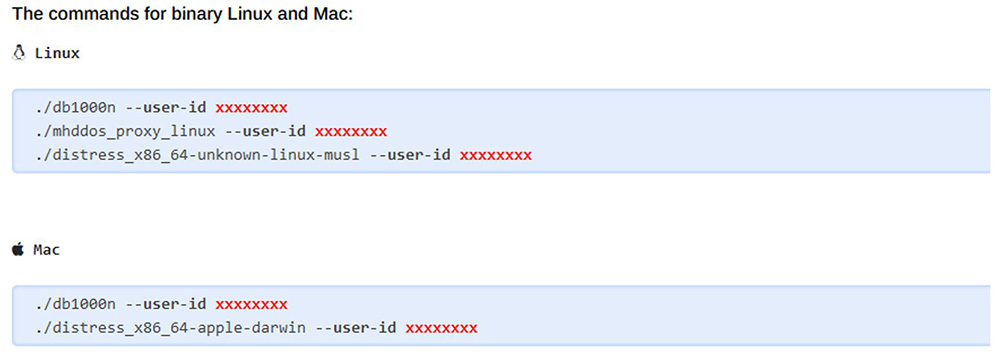
Figure 12: Instructions how to use IT Army ID with IT Army provided and maintained expert-level command line tools
The impact of the IT Army Kit and the improved attack tools extends beyond the immediate operational benefits. It represents an innovative approach to cyber warfare and digital activism, setting a precedent for how similar movements might organize and mobilize in the future. By empowering individuals with the means to participate in cyber operations, the IT Army is expanding its capabilities and fostering a sense of community and shared purpose among volunteers worldwide.
Instructions for Deploying Attack Servers
Besides tooling and offering education on the use of DDoS attack tools, the website of the IT Army of Ukraine also contains a section describing how to obtain free, but capable resources through abusing trials of well-known cloud providers such as Google Cloud, Amazon, Azure, Hetzner, and Digital Ocean.
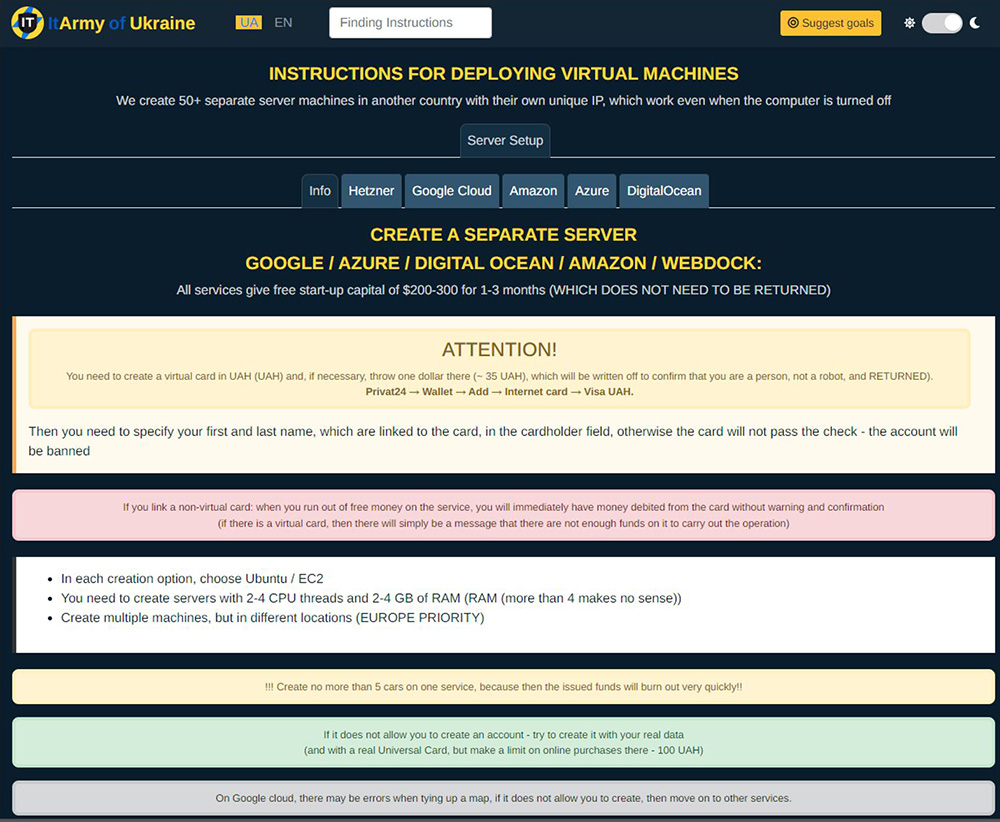
Figure 13: IT Army of Ukraine instructions to create and deploy virtual machines in several leading cloud providers
The information includes ‘best practices’ on how to activate the cloud providers’ trial periods using virtual, pre-paid credit cards backed by only a single dollar of credit. They also provide guidance on which server tiers are most efficient and where in the world it is best to host them.
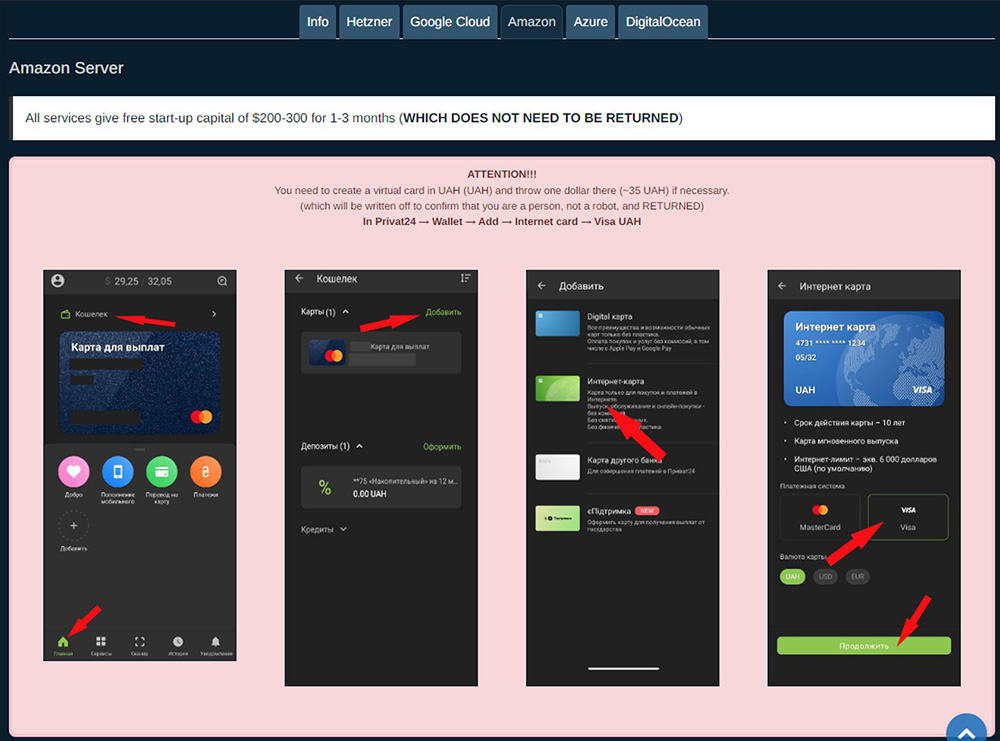
Figure 14: Detailed instructions how to use virtual credit cards to create a free trial in Amazon Cloud
Conclusion
The IT Army of Ukraine’s innovative approach to engaging the public in cyber warfare has significantly contributed to the democratization of DDoS attacks. By lowering barriers to entry, leveraging crowdsourcing, providing educational resources, and normalizing cyber volunteerism, this movement has expanded the scope of who can participate in cyber operations and how these operations can be conducted. As the digital domain continues to evolve, the lessons learned from the IT Army’s campaign will undoubtedly influence the strategies of future cyber engagements, highlighting the growing importance of collective action and public participation in shaping the cyber landscape.



