In the ever-evolving landscape of the digital world, denial of service (DoS) and distributed denial of service (DDoS) attacks persist as formidable challenges. These attacks aim to incapacitate online services by flooding them with an overwhelming volume of traffic from multiple sources. The scale and complexity of these attacks have grown exponentially, posing a significant threat to enterprises of all sizes.
The urgency for a thorough understanding and strategic implementation of DDoS attack prevention measures is more critical than ever. This article provides an in-depth exploration of essential strategies and industry best practices. These are designed to bolster your network’s defenses and ensure the resilience of your online operations against the escalating threat of DDoS attacks.
We will delve into the technical nuances of DDoS attacks and provide actionable insights on how to fortify your digital infrastructure. Our goal is to equip you with the knowledge and tools to proactively defend against and effectively mitigate the impact of DDoS attacks.
DDoS attacks are a sophisticated form of cyber-attacks that aim to disrupt the normal functioning of a network, service, or server by overwhelming it with a flood of internet traffic. These attacks are “distributed” because they originate from multiple sources, often thousands of devices in a botnet, which makes them difficult to stop. The sheer volume of traffic can exceed the processing capacity of the target system, causing it to slow down or even crash. DDoS attacks exploit the fundamental way that the internet communicates: the protocol suite known as TCP/IP.
In a typical DDoS attack, the attacker begins by exploiting a vulnerability in one computer system and making it the DDoS master. The attack master, also known as the botmaster, identifies and infects other vulnerable systems with malware. These infected systems, often referred to as ‘zombies’, are then remotely controlled by the botmaster, forming a network of compromised systems, or a ‘botnet’.
The botmaster then commands this network of bots to send a flood of requests to a specific target. This could be a single target, such as a website, or multiple targets within a network. The flood of incoming messages to the target system essentially forces it to shut down, denying service to the system's legitimate users. This is achieved by exhausting the target’s resources such as bandwidth, processing power, or memory.
DDoS attacks can be broadly classified into four types: volumetric attacks, protocol attacks, application layer attacks, and multi-vector attacks.
Application-Layer Attacks
These attacks target the layer where web pages are generated on the server and delivered to the user. They aim to exhaust the server’s resources, making the targeted application slow or unresponsive. Signs of an application-layer attack include unusually slow network periphery, despite having normal network traffic. These attacks are often more difficult to detect because they involve what appear to be legitimate requests, but in such volume that the server cannot handle them.
Volumetric Attacks
These attacks aim to saturate the bandwidth of the attacked site, and involve overloading the network with packets, causing the network to become slow or unresponsive. A sudden spike in traffic could be a sign of a volumetric attack. These attacks typically involve the attacker spoofing the IP addresses of the packets, making it appear as if the traffic is coming from legitimate users.
Protocol Attacks
These attacks consume all the processing capacity of a web server or an intermediate resource like a firewall. Symptoms may include a sudden server reboot or drop in connection in the firewall. Protocol attacks exploit weaknesses in the network protocols to overwhelm the target with packets, causing it to respond to bogus requests and thus exhausting its resources.
Multi-Vector Attacks
In recent years, we have seen an increase in multi-vector DDoS attacks. These sophisticated attacks combine all three types of DDoS attacks, making them particularly difficult to mitigate. They can also switch tactics mid-attack, further complicating the defense process.
Differentiating between normal traffic surges and potential DDoS activity can be challenging. However, there are a few key differences. Normal traffic surges typically occur sporadically and are often tied to specific events or times of day. DDoS traffic, on the other hand, is usually more sustained and doesn't follow typical user behavior patterns. Recognizing a DDoS attack involves continuous monitoring, understanding your network’s normal behavior, and being able to identify anomalies such as:
Slow Network Performance
DDoS attacks often cause network performance to degrade, resulting in slow loading times or difficulty accessing network resources. While this could be due to a variety of reasons, a sustained slowdown could indicate a DDoS attack. It’s important to note that not all performance issues are indicative of a DDoS attack. However, if the slowdown is severe and persists despite your best troubleshooting efforts, it may be time to consider the possibility of a DDoS attack.
Unusual Traffic Patterns
A sudden, unexpected surge in network traffic is often the first sign of a DDoS attack. This could manifest as an unusual spike in requests to a particular server or service. Monitoring traffic patterns and understanding your network’s baseline is crucial for detecting these anomalies. Network monitoring tools can provide real-time analysis of your network traffic and alert you to any significant deviations from the norm.
Unavailability of a Particular Service
If a specific service or website becomes unavailable, it could be under a DDoS attack. This is especially true if the service remains inaccessible despite repeated attempts to connect. Regularly testing your services for availability can help you detect a potential DDoS attack early.
Increase in Spam Emails
Some DDoS attacks are preceded by a spike in spam emails. This could be an attempt to distract IT staff while the actual DDoS attack is launched. Therefore, a sudden increase in spam could be indicative of a brewing DDoS attack.
Disproportionate Increase in Requests
During a DDoS attack, you may notice a disproportionate increase in requests to a single endpoint or service. This could be a sign that attackers are trying to overwhelm a specific part of your network.
Unusual Device Behavior
Devices on your network may start to behave unusually during a DDoS attack. For example, if your routers or firewalls are processing more network traffic than usual, this could be a sign of a DDoS attack.
Network Bottlenecks
DDoS attacks can cause network bottlenecks, which can slow down your entire network. If you notice that certain parts of your network are slower than others, this could be a sign of a DDoS attack.
Preventing DDoS attacks involves a combination of traditional security measures, a well-prepared response plan, a robust anti-DDoS architecture, adherence to network and application security best practices, and regular system updates and patches. By implementing these measures, you can significantly enhance your defenses against DDoS attacks and ensure the resilience and availability of your online operations.
Start With Traditional Security Measures
Traditional security measures such as firewalls with Access Control Lists (ACLs) and static signature-based protections are the first line of defense against DDoS attacks. However, these measures alone are not always sufficient as DDoS attacks often target applications and services at the application layer (Layer 4-7 of the OSI model). Therefore, it’s crucial to ensure protections are in place for non-firewall protected services like HTTP, FTP, and SMTP.
Craft a DDoS Response Plan
A comprehensive response plan for DDoS attacks is essential. This plan should outline the steps to take in the event of an attack to minimize damage and downtime. It should include procedures for identifying the attack, notifying the appropriate personnel, isolating affected systems, and implementing mitigation strategies. Regular testing and updating of this plan are also crucial to ensure its effectiveness.
Follow Network & Application Security Best Practices
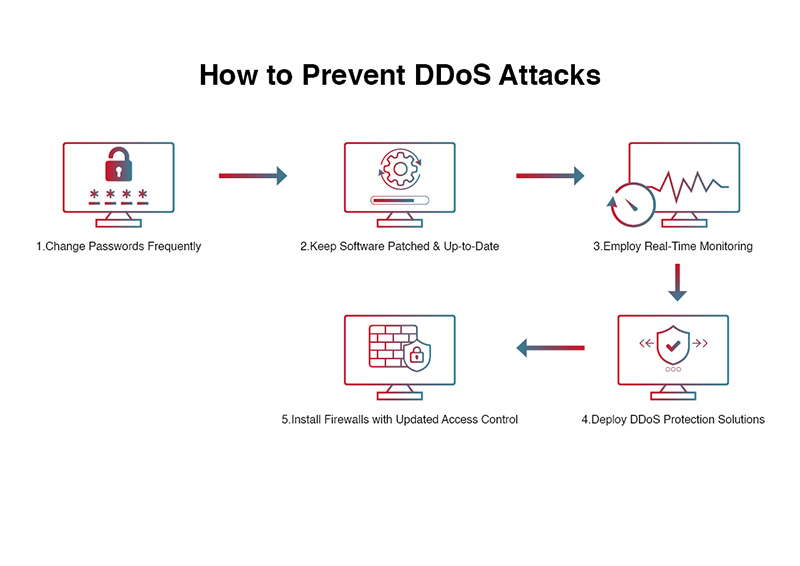
Implementing best practices for network and application security can significantly reduce the risk of a DDoS attack. These include changing passwords frequently to reduce the risk of unauthorized access, regularly scanning for vulnerabilities and patching any that are found promptly, deploying anti-malware and additional DDoS protection solutions/services, and implementing firewalls with up-to-date access control lists.
Vary Your Anti-DDoS Architecture
Deploying a combination of DDoS protection services, firewalls, web application firewalls, routers, and switches can help mitigate threats. This multi-layered approach ensures that even if one layer is compromised, others remain to protect the system. Consider solutions that offer real-time monitoring capabilities to detect malicious requests or data before they reach your application or service.
Stay Current on System Updates & Patches
Keeping all networks and system operating systems up to date with the latest security patches is crucial. Many DDoS attacks exploit known vulnerabilities in software that have already been patched by the software provider. Therefore, regular updates and patches can protect your systems from these types of attacks. Be mindful of attacks that consume resources of stateful devices; implement solutions minimizing allocated resources close to completion information/threat state of each client connection.
Radware offers a suite of advanced DDoS prevention tools that play a crucial role in safeguarding digital assets against the evolving landscape of DDoS threats. These tools are designed to provide comprehensive protection against a wide range of DDoS attacks, ensuring the resilience and availability of your online operations.
Emergency Response Team
Radware’s Emergency Response Team (ERT) is a dedicated group of security experts providing round-the-clock support and mitigation services for a wide range of application and network-layer DDoS attacks. With a team of experienced security engineers, the ERT offers immediate assistance and specialized mitigation techniques for organizations under threat from DoS, DDoS attacks, or malware outbreaks.
The team handles various security events, including malware outbreaks and application exploits, and uses their industry-leading expertise, best practices, and deep knowledge of threats, attack tools, intelligence, and mitigation technologies to combat common and emerging attacks daily. During prolonged, complex attacks, the ERT provides the necessary expertise and service to quickly restore operations by swiftly mitigating DDoS attacks.
Specific Tools and Technologies
Among Radware’s suite of tools, DefensePro stands out for its advanced DDoS prevention and protection capabilities. DefensePro uses patented, behavioral-based algorithms to automatically block the most advanced threats in real-time. It is capable of handling a wide range of attacks, including volumetric attacks, application-layer attacks, and ‘low-and-slow’ attack tactics.
In addition to DefensePro, Radware also offers cloud-based DDoS protection services. These services use advanced behavioral algorithms to detect and mitigate DDoS attacks at any level, providing infrastructure DDoS protection and web DDoS protection. They offer an additional layer dedicated to detecting and mitigating sophisticated application-layer DDoS attacks.
Continuous Innovation and 24/7 Support
At Radware, we are committed to continuous innovation, constantly updating our tools and technologies to stay ahead of the evolving threat landscape. We offer 24/7 support, ensuring that organizations have the help they need, when they need it. With Radware’s advanced DDoS prevention tools and dedicated support, organizations can stay ahead of the curve in DDoS threat prevention and response.
By leveraging these tools and following the best practices outlined in this article, businesses can significantly enhance their defenses against DDoS attacks and ensure the resilience and availability of their online operations.
Comprehensive Defense Mechanism
Radware’s solutions offer a comprehensive defense mechanism, integrating adaptive behavioral-based detection with real-time signature recognition to effectively mitigate attacks. This unique approach allows Radware’s tools to accurately detect and block even the most advanced threats in real-time, including burst and DNS attacks, web DDoS attacks, IoT botnets, and ransom DDoS.